
Aqua Security provides cloud-native security solutions, protecting containers, Kubernetes, and serverless environments across the development lifecycle.
Text Here

Market Leadership:
• Leader in the 2024 Gartner Magic Quadrant for Cloud-Native Security.
• Strong performer in IDC’s 2024 Container Security MarketScape.
• Recognized in China IDC’s 2024 Cloud Security Solutions Report.
• Highlighted in Forrester’s 2024 Cloud Workload Security Wave Report.
Video
Flagship Products:
Key Features:
| 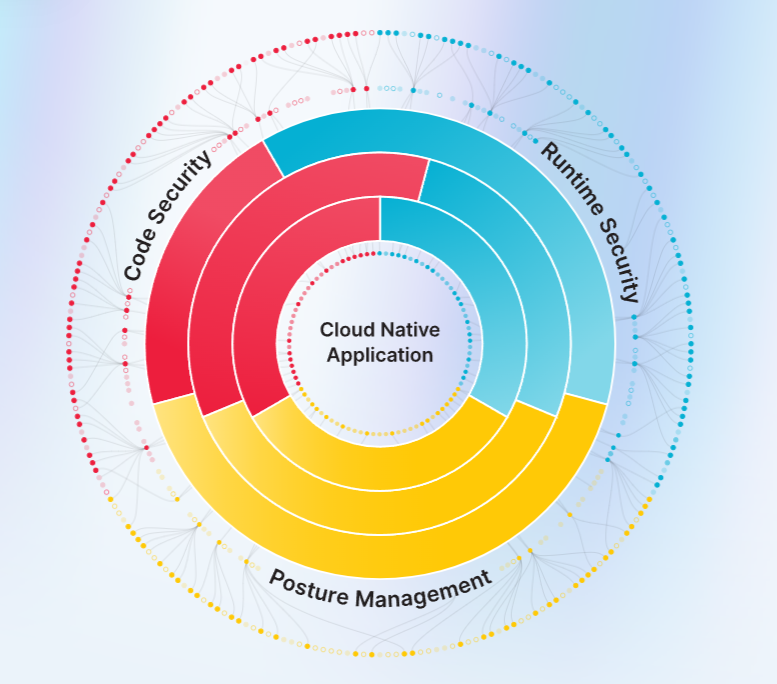 |
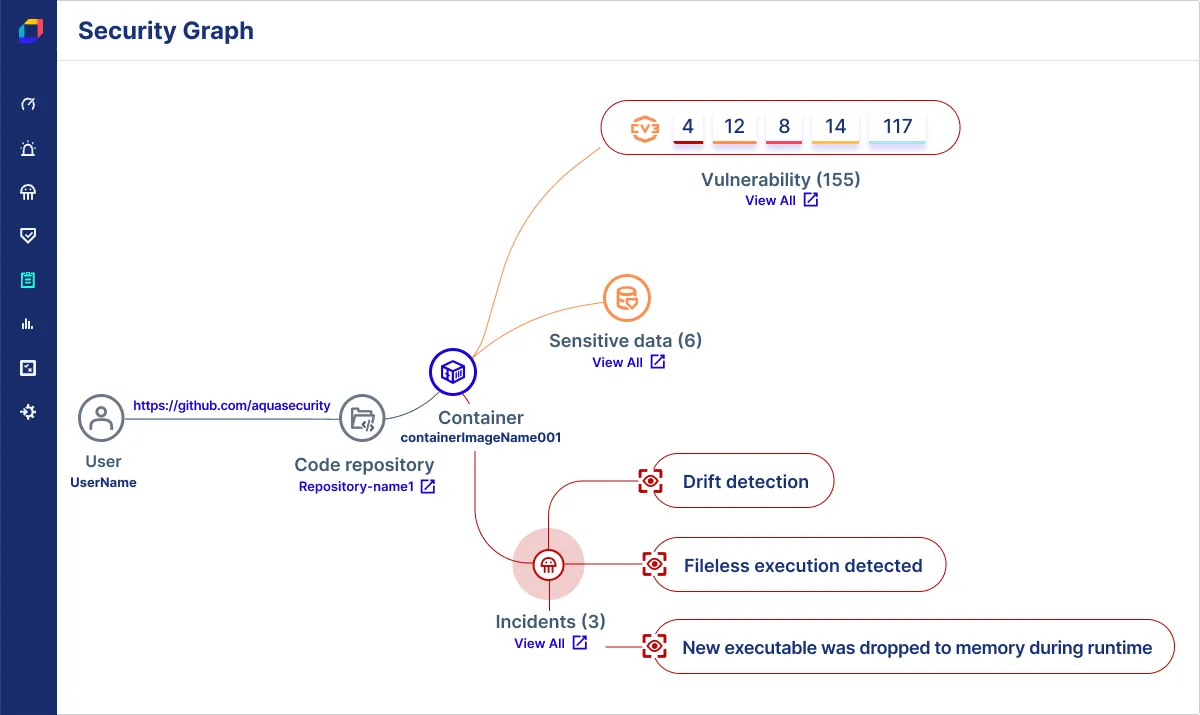 | 2. Aqua CSPM: Cloud security posture management platform. Key Features:
|
Key Features:
| 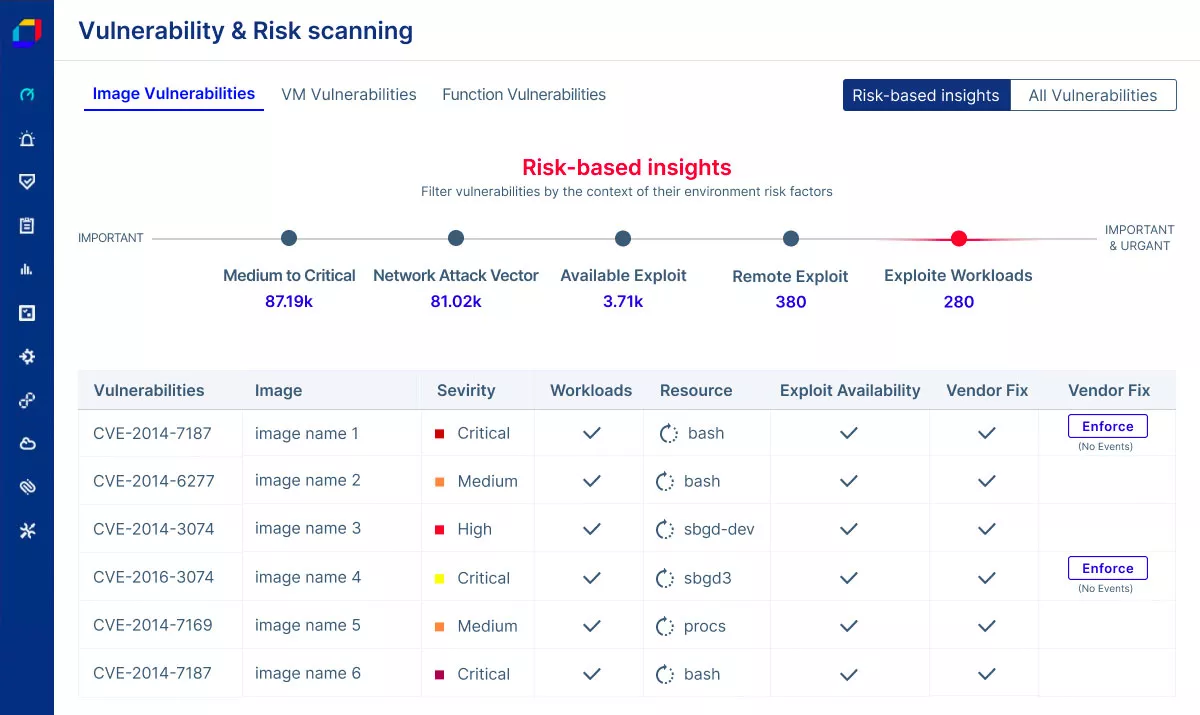 |
- Aqua Serverless Security: Protection for Function-as-a-Service (FaaS) environments.
Key Features:
- Function scanning for vulnerabilities and dependencies.
- Privilege control to enforce least privilege.
- Event monitoring for suspicious activities.
- Compliance reporting for serverless workloads.
- Integration with AWS Lambda, Azure Functions, and Google Cloud Functions.
User Benefits: Aqua Security ensures secure cloud-native deployments, reduces vulnerabilities, and simplifies compliance for DevSecOps teams.