
Delivering modern cybersecurity by proactively safeguarding critical data and IP.
To foster safe and trusting environments through a converged platform that understands digital identities and their cyber behaviors to protect employees and critical data everywhere, Forcepoint delivers modern cybersecurity solutions to protect the below area:
| Data & IP: | Data Loss Protection > | Cloud Access Security Broker > | Email Security > |
| Cloud & Network: | Web Security > | Next Generation Firewall > | Cloud Access Security Broker > |
| Insider Threat: | Behavioral Analytics > | Insider Threat > |
The vision of Forcepoint is to understand the world’s cyber behaviors to stop the bad and free the good. The Mission is to foster safe and trusting environments through a converged platform that understands digital identities and their cyber behaviors to protect employees and critical data everywhere. Attentive, Optimistic, Committed, Imaginative and trustworthy is the Values. Then what stop you, schedule a Demo now.
Data protection
9x Gartner Magic Quadrant Leader for DLP
WHY FORCEPOINT DLP?
Control all your data with one single policy
| 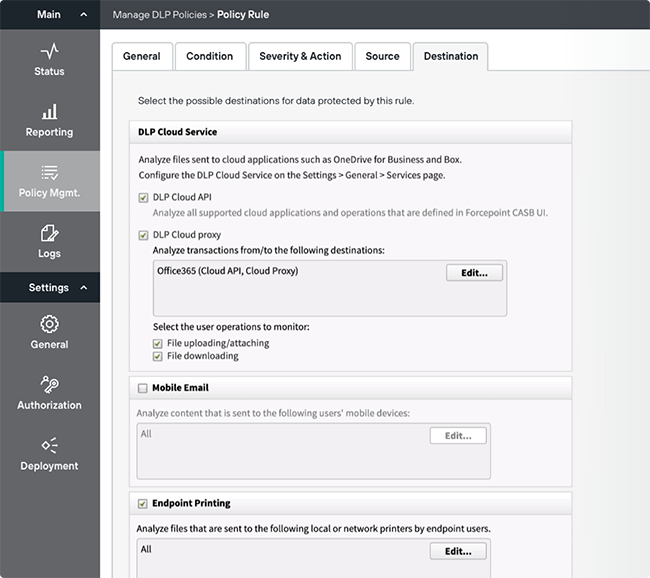 |
Simplify compliance with predefined policies
| 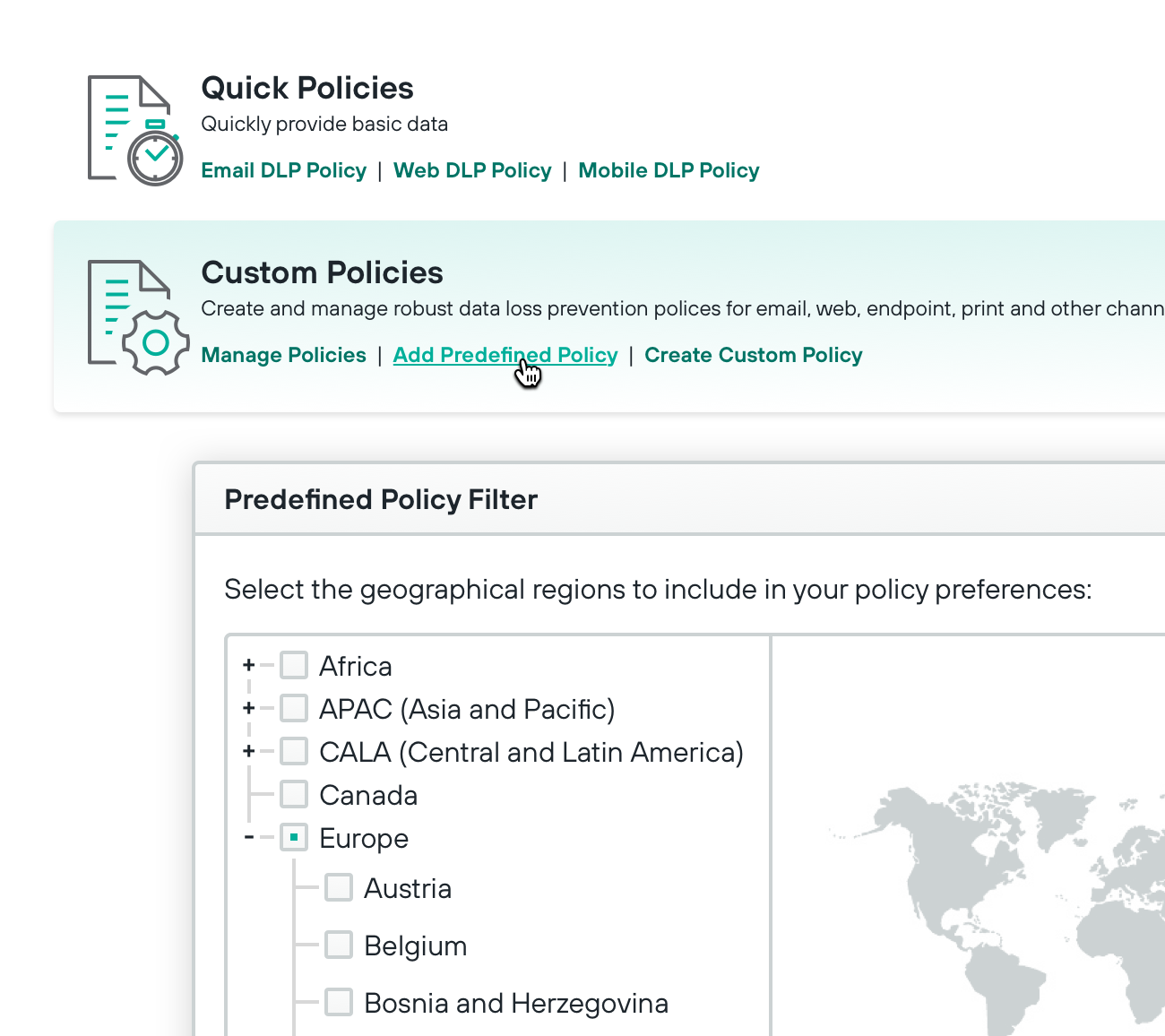 |
Protect critical intellectual property with unsurpassed accuracy
| 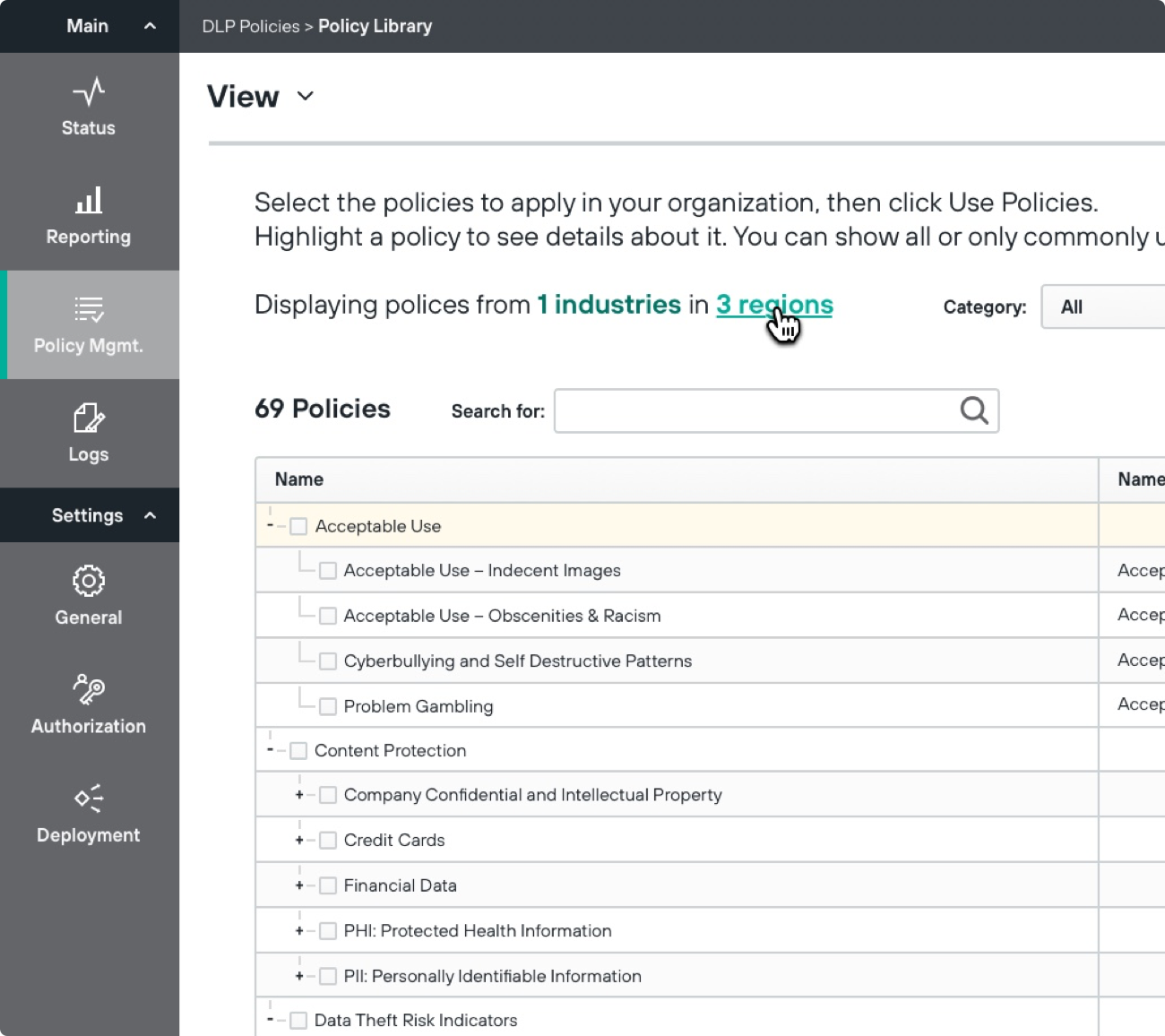 |
Prevent data breaches automatically
| 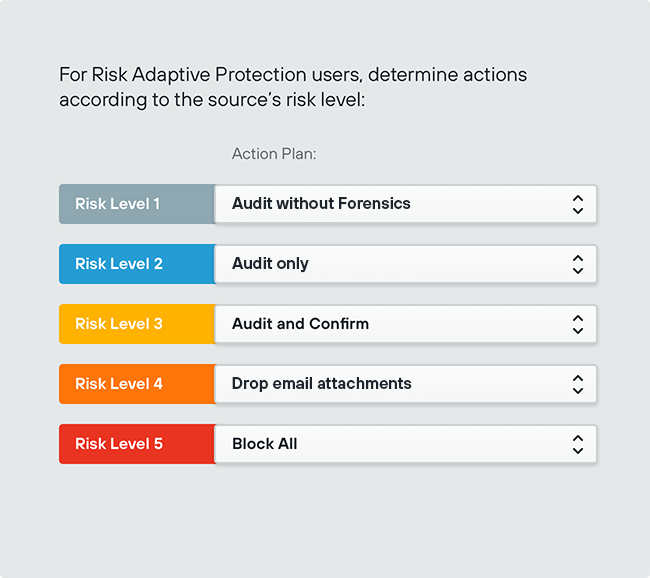 |
Cloud security
Complete visibility into shadow IT
|  |
Prevent compromised accounts
|  |
Secure mobile access to cloud apps
|  |
Edge security
Replace MPLS and go direct to cloud
|  |
Stop evasions that bypass your IPS
|  |
Respond to incidents in minutes, not hours
|  |
Advanced Malware Detection
Detect evasive malware others cannot seeIt’s become increasingly difficult to identify the malware components of advanced threats, mostly due to the evolution of evasion tactics and technology by criminal and nation-state threat actors. Unmatched Accuracy Forcepoint Advanced Malware Detection technology is unmatched in security efficacy. Even highly evasive threats are revealed through Deep Content Inspection of activity at multiple levels, dormant code, and other indicators often overlooked by traditional sandbox security technologies. Zero-False Positives Eliminate the distraction of False Positive results with AMD. This means your incident response team can spend its limited time responding to actual threats, not chasing down false positives and searching for indicators of compromise (IOCs). |
